Cyclomatic Complexity in Software Development and Its Impact on Cybersecurity
Understanding Cyclomatic Complexity
Introduction
The concept of cyclomatic complexity, introduced by Thomas J. McCabe in 1976, is crucial for grasping code complexity and plays a significant role in cybersecurity.
This article will delve into cyclomatic complexity, its effects on code quality, and its connection to cybersecurity. We’ll also explore examples of how cyclomatic complexity can impact software security and ways to mitigate its risks.
Grasping Cyclomatic Complexity
Cyclomatic complexity measures the number of independent execution paths through a program’s source code.
Fundamentally, it assesses software’s flow control complexity by counting decision-making structures like if, else, switch, while, and for statements.
A higher cyclomatic complexity score signals more complex code, which can be more challenging to understand and maintain.
Cyclomatic Complexity and Code Quality
Code with high cyclomatic complexity often indicates poor quality. It’s more error-prone due to its challenging readability, comprehension, and modification. In software development, simpler code is typically preferred as it’s easier to maintain and less likely to contain errors.
Let’s examine some examples to illustrate better how cyclomatic complexity can influence code quality.
Python example
Bad complexity
Here, a code snippet performs multiple tasks with multiple conditions, making it hard to understand and maintain.
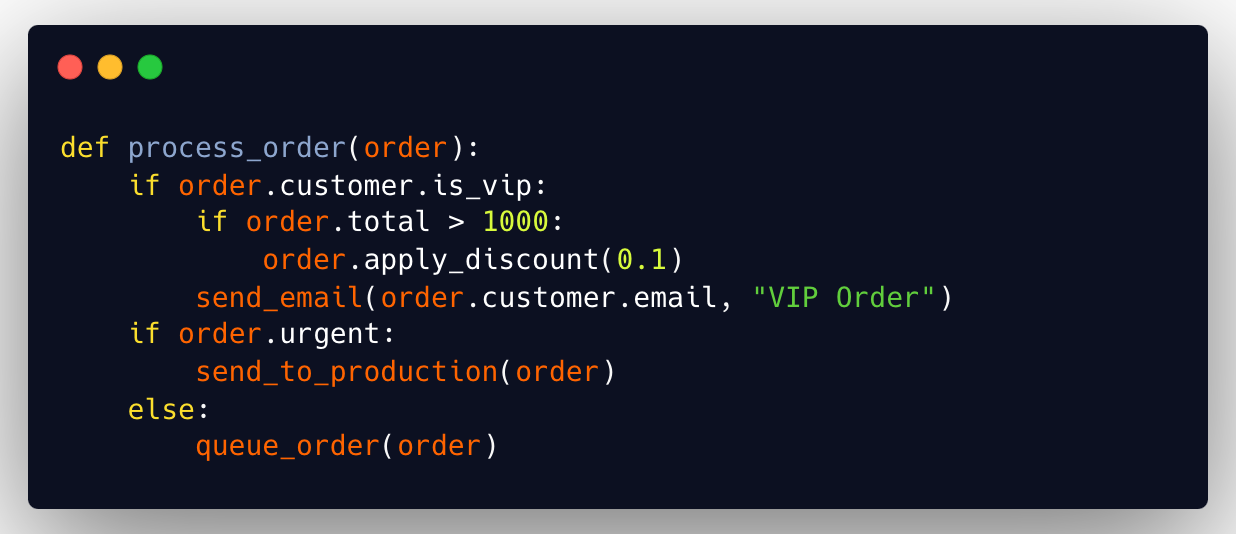
Good complexity
Decomposing functions into smaller, more specific parts.
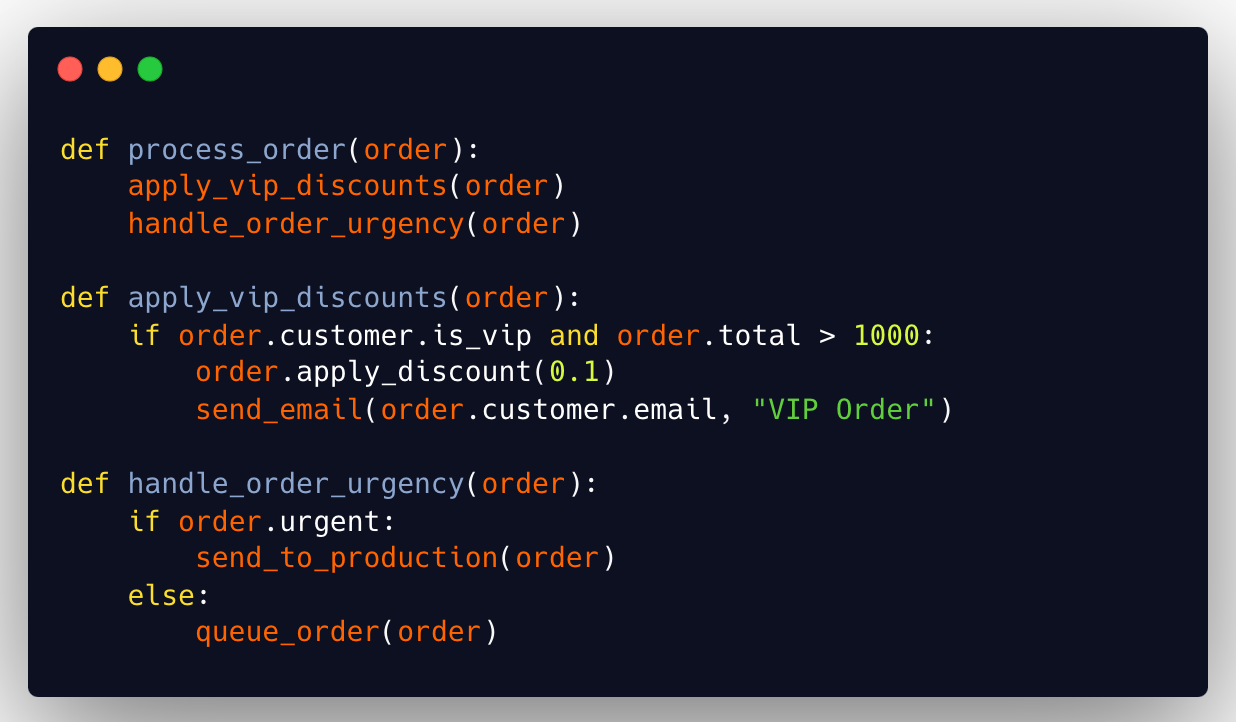
The cyclomatic complexity is significantly reduced by breaking down the original function into smaller, more specific parts. Each function is responsible for a particular task, making the code more readable and easier to maintain.
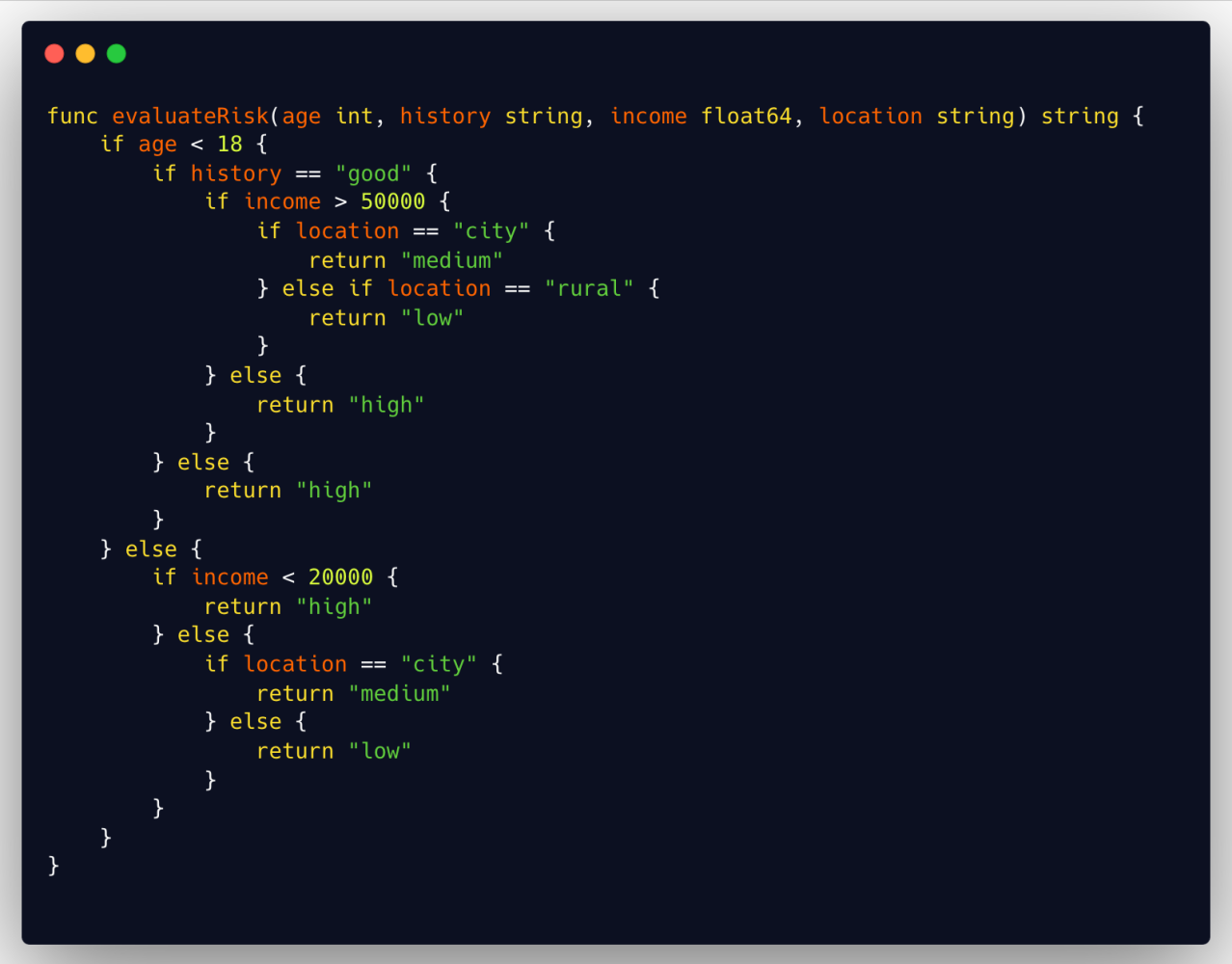
Golang example
Bad complexity
This code has multiple branching and nested conditions, significantly increasing its cyclomatic complexity. This makes it difficult to understand, test, and maintain. Each new condition adds one more path through the code, raising the possibility of errors and making it harder to detect security issues.
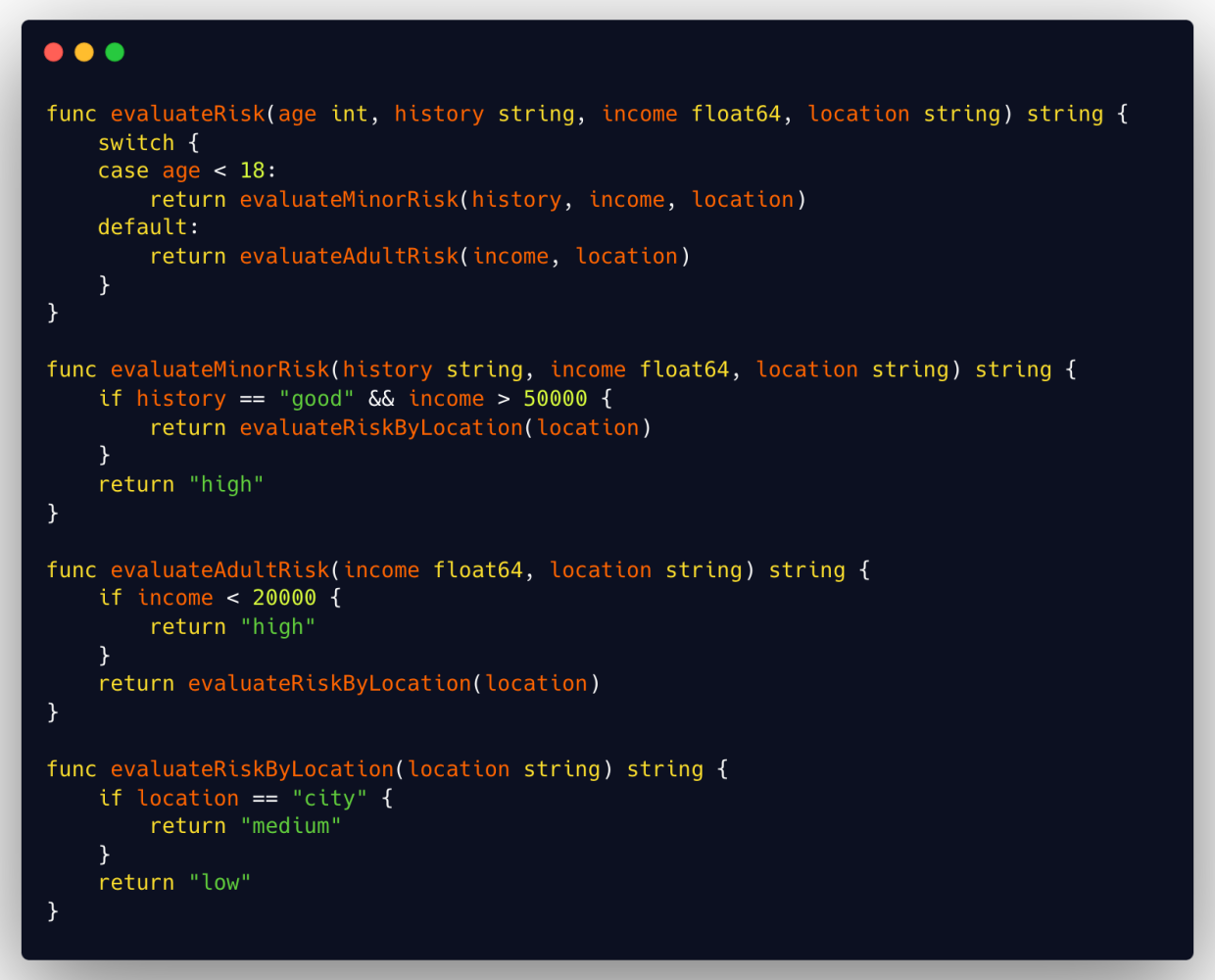
Good complexity
This code has been refactored to reduce its cyclomatic complexity. Parts of the logic have been extracted into separate functions, making each function more straightforward and with a single responsibility.
Switches and separate functions make the code easier to understand and maintain, as well as test and debug.
This structure also makes identifying and rectifying potential security vulnerabilities easier, as each function focuses on a specific aspect of the risk evaluation logic.
Cyclomatic Complexity and Cybersecurity
High cyclomatic complexity can significantly impact the cybersecurity of software. Here are some ways in which high cyclomatic complexity can affect software security:
-
Human Errors: More complex code is more complicated to understand, making it more prone to errors during development and maintenance. These errors can create unintended vulnerabilities.
-
Code Review Challenges: Code review is crucial for identifying vulnerabilities. High cyclomatic complexity can make code reviews more challenging and less effective.
-
Testing and Code Analysis: Automated testing and code analysis tools may struggle to properly analyze codes with high complexity, leaving potential vulnerabilities undetected.
Cyclomatic Complexity and Security Failures
Security failures often stem from coding errors. High cyclomatic complexity increases the likelihood of security flaws. Some common vulnerabilities related to cyclomatic complexity include:
- SQL Injections: Complex codes may not properly handle user inputs, leading to SQL injection vulnerabilities.
- Buffer Overflow Errors: Excessive complexity in data handling can lead to poor boundary checks, resulting in buffer overflow errors.
- Authentication and Session Management Failures: Complex codes in authentication systems can contain critical flaws, compromising user security.
- Access Control Issues: High cyclomatic complexity can lead to errors in permission management and access control, often the source of vertical privilege escalations.
- Code Injection Vulnerabilities: High cyclomatic complexity can lead to complex flow control, resulting in code injection vulnerabilities due to poor management of user inputs.
- Session Management Issues: High cyclomatic complexity can lead to session management and authentication errors, often the source of horizontal privilege escalations.
While there are other vulnerabilities, these are some of the most common ones related to cyclomatic complexity.
Examples of Vulnerabilities Related to Cyclomatic Complexity (Python)
Web Authentication Flows
High Cyclomatic Complexity
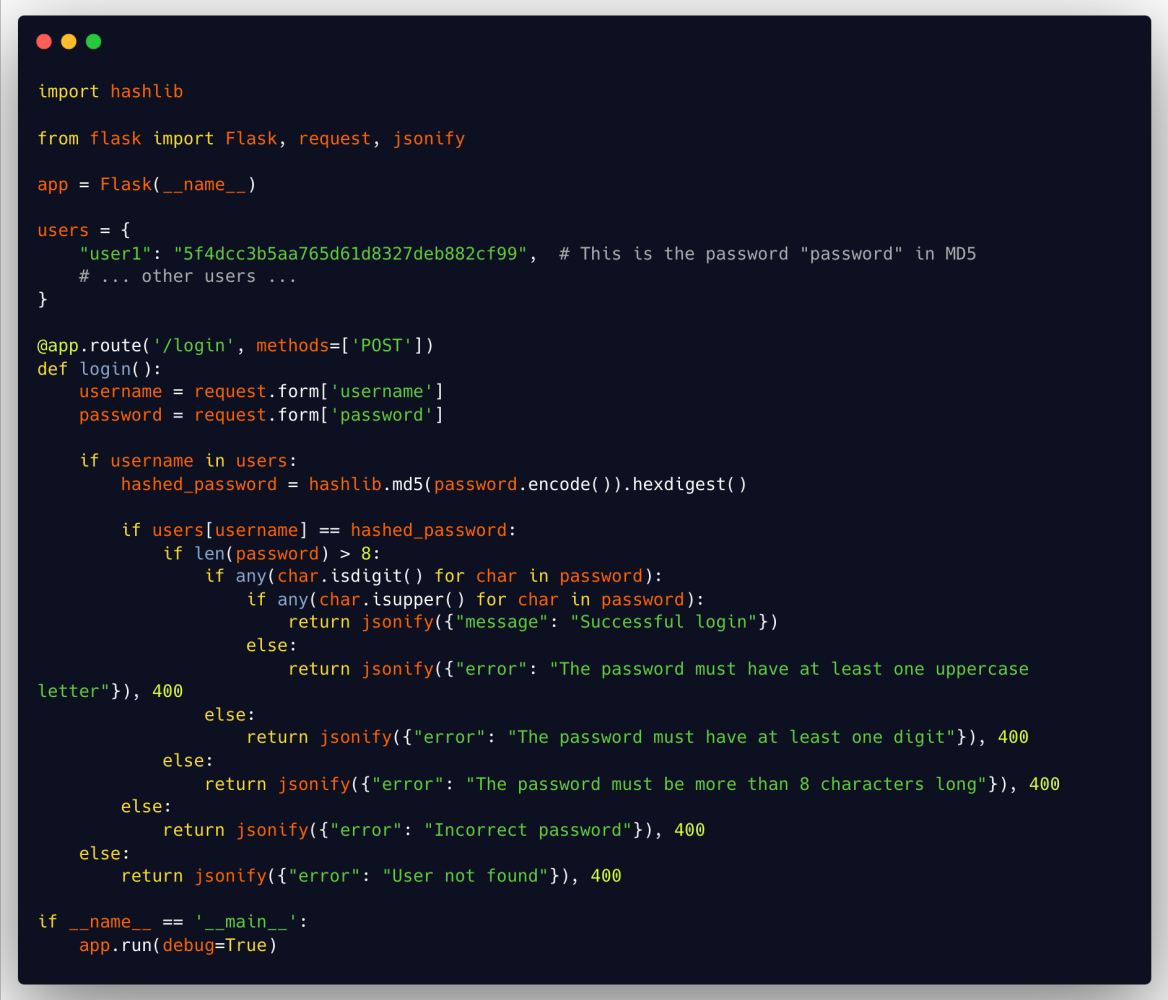
In the following example, a complex authentication code may contain security vulnerabilities. High cyclomatic complexity can make it harder to detect and correct these vulnerabilities.
- This code has high cyclomatic complexity due to multiple nested conditions and branches.
- It uses MD5 for the password, which is not secure.
- Password validation is performed after verifying if the user exists and the password matches, which is not a recommended practice.
Low Cyclomatic Complexity
In this example, the authentication code has been simplified and refactored to reduce cyclomatic complexity. This makes it easier to understand, test, and maintain, decreasing the likelihood of security vulnerabilities.
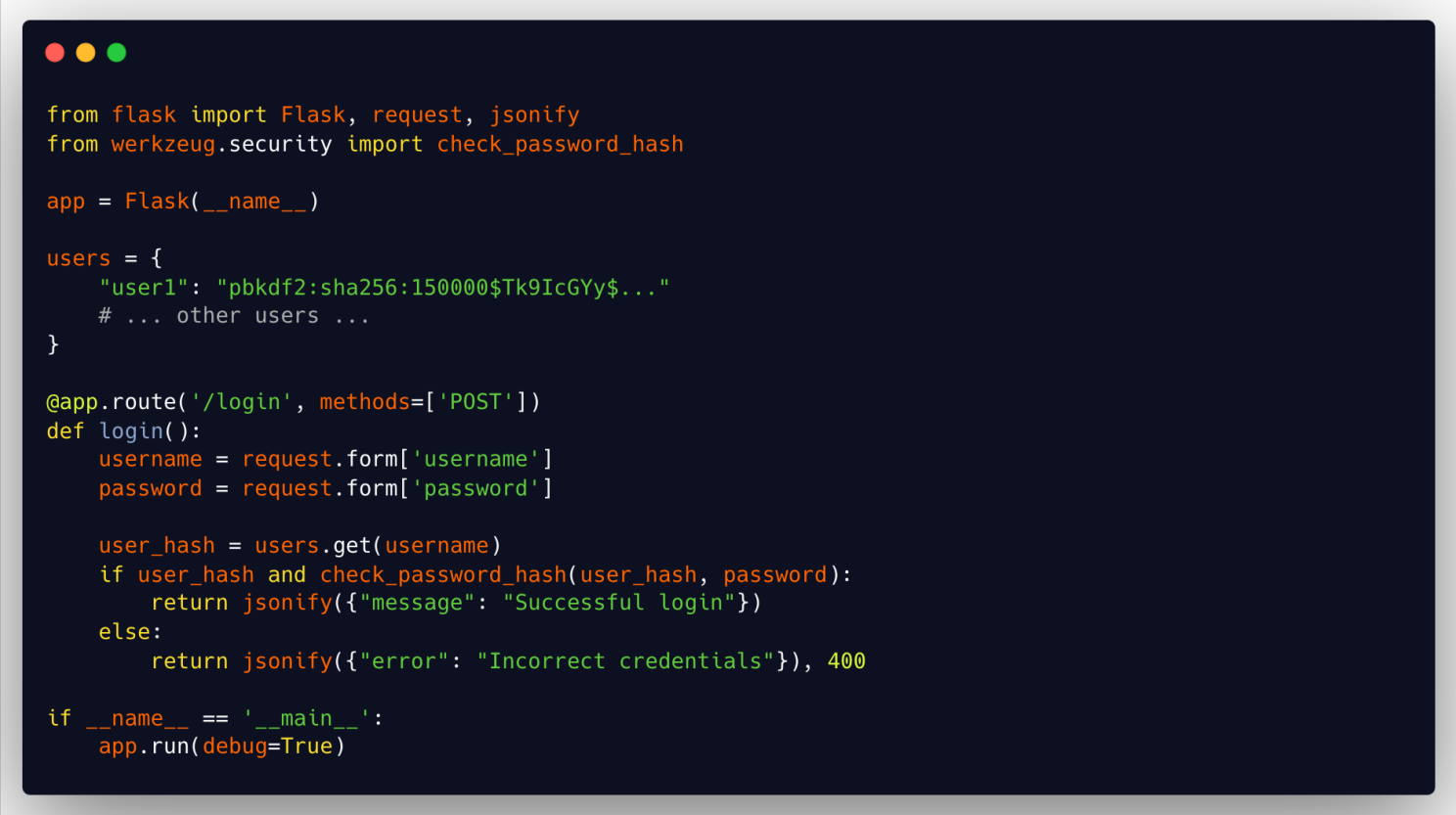
- Cyclomatic complexity is significantly reduced due to the elimination of unnecessary nested conditions.
- Uses werkzeug.security.check_password_hash for more secure password verification.
- Improves security by not revealing whether a specific username exists or not.
Command execution
High Cyclomatic Complexity
This example demonstrates a script that performs operations based on user input, with a complex control structure and a critical vulnerability:
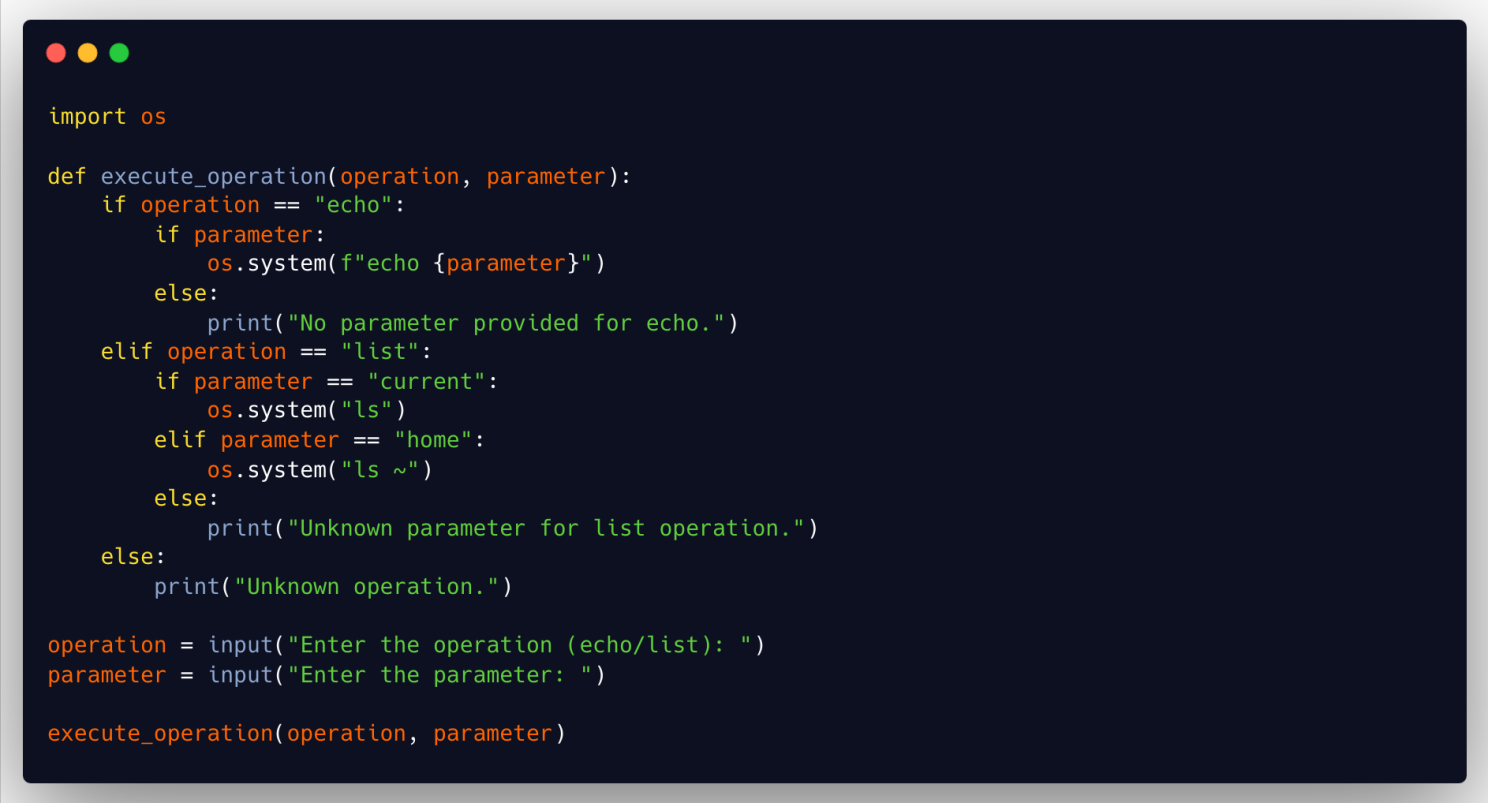
- This code has high cyclomatic complexity due to multiple decision branches.
- It uses
os.system, which is dangerous if combined with unsanitized inputs, allowing the execution of arbitrary commands.
Low Cyclomatic Complexity
Here’s a safer approach with lower cyclomatic complexity.
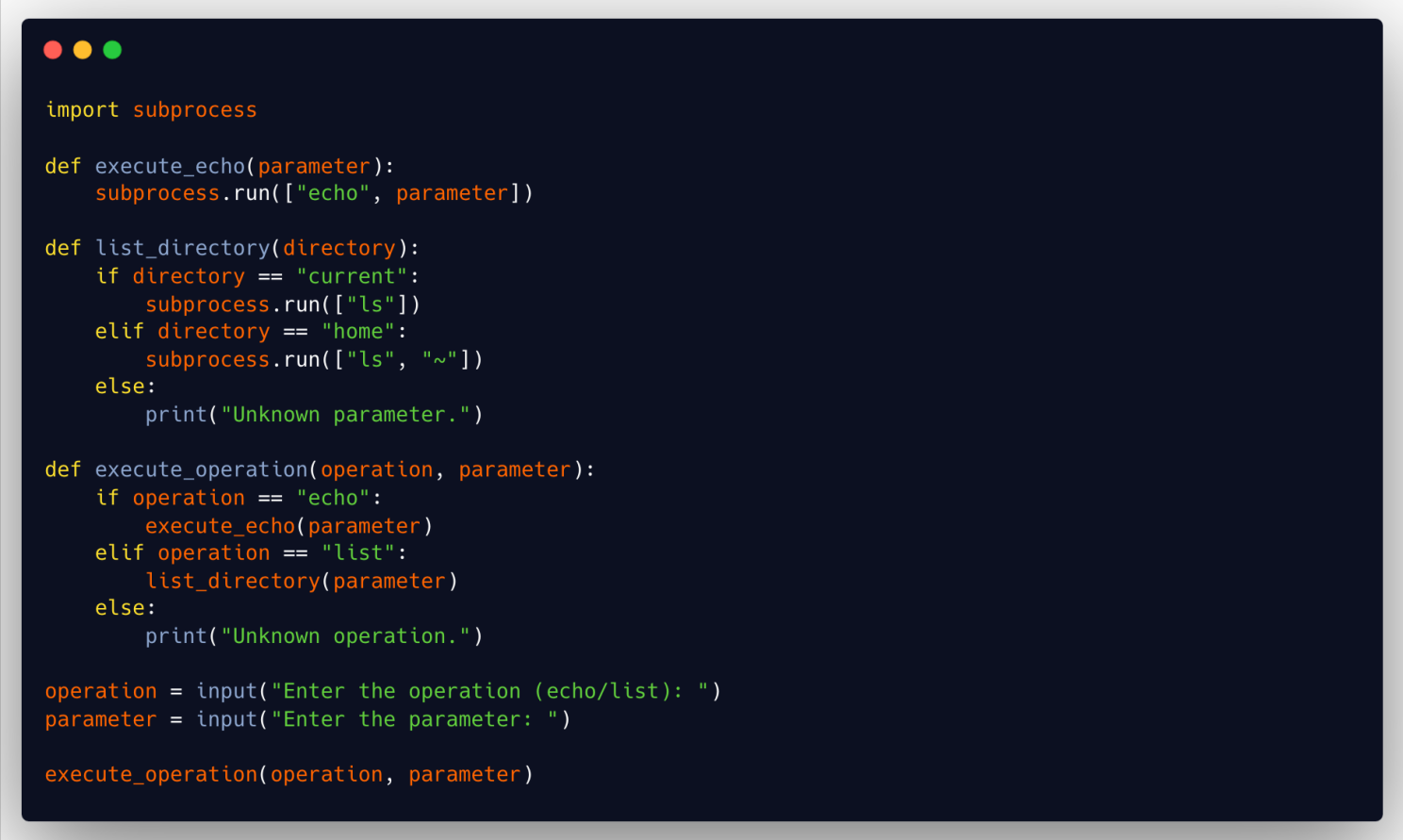
- The cyclomatic complexity is reduced by breaking the logic into smaller, clearer functions.
- It uses
subprocess.run, is safer thanos.system, and prevents insecure command execution. - Separating the operations into different functions makes the code easier to understand and maintain.
Examples of Vulnerabilities Related to Cyclomatic Complexity (Golang)
Arbitrary Command Execution
This example in Go demonstrates a function that processes user input to execute system commands. The complexity arises from multiple conditional branches and direct command execution based on user input.
High Cyclomatic Complexity
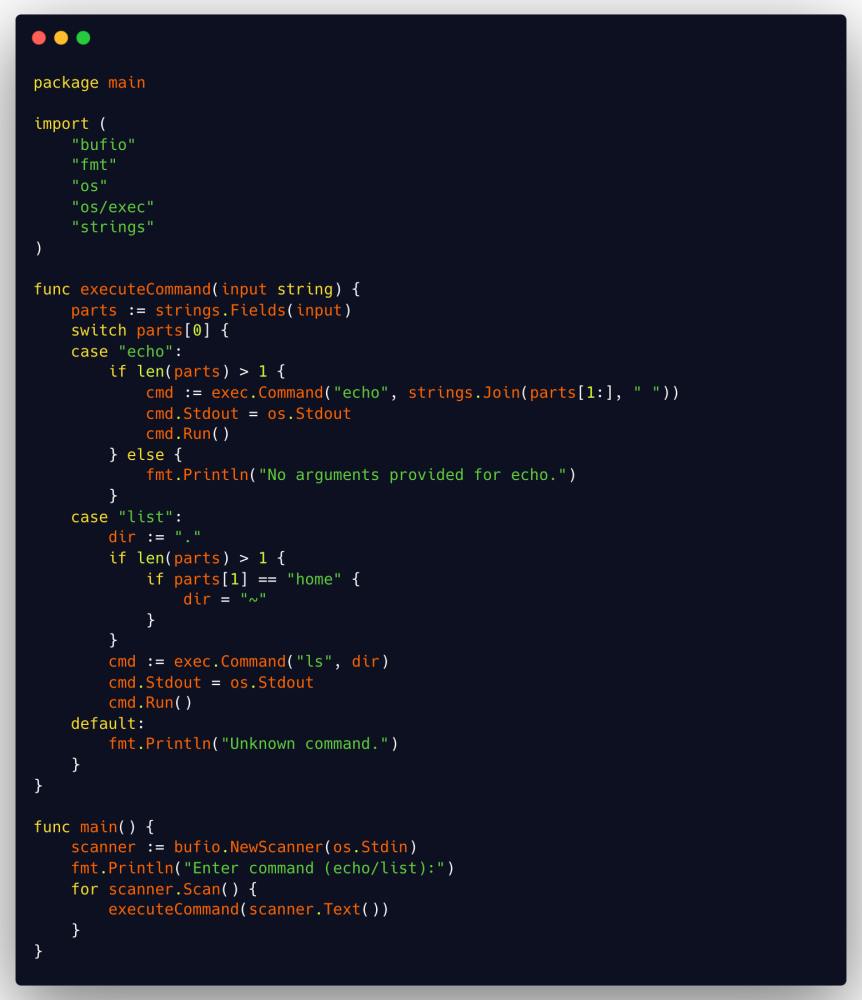
- The function executeCommand processes user input and directly executes system commands based on this input.
- Using
exec.Commandwith unsanitized user input introduces a significant security risk, as it can lead to arbitrary command execution. - The complexity of handling different commands in the same function increases the risk of errors and makes the code harder to audit for security issues.
Low cyclomatic complexity
Here’s a safer approach with lower cyclomatic complexity:
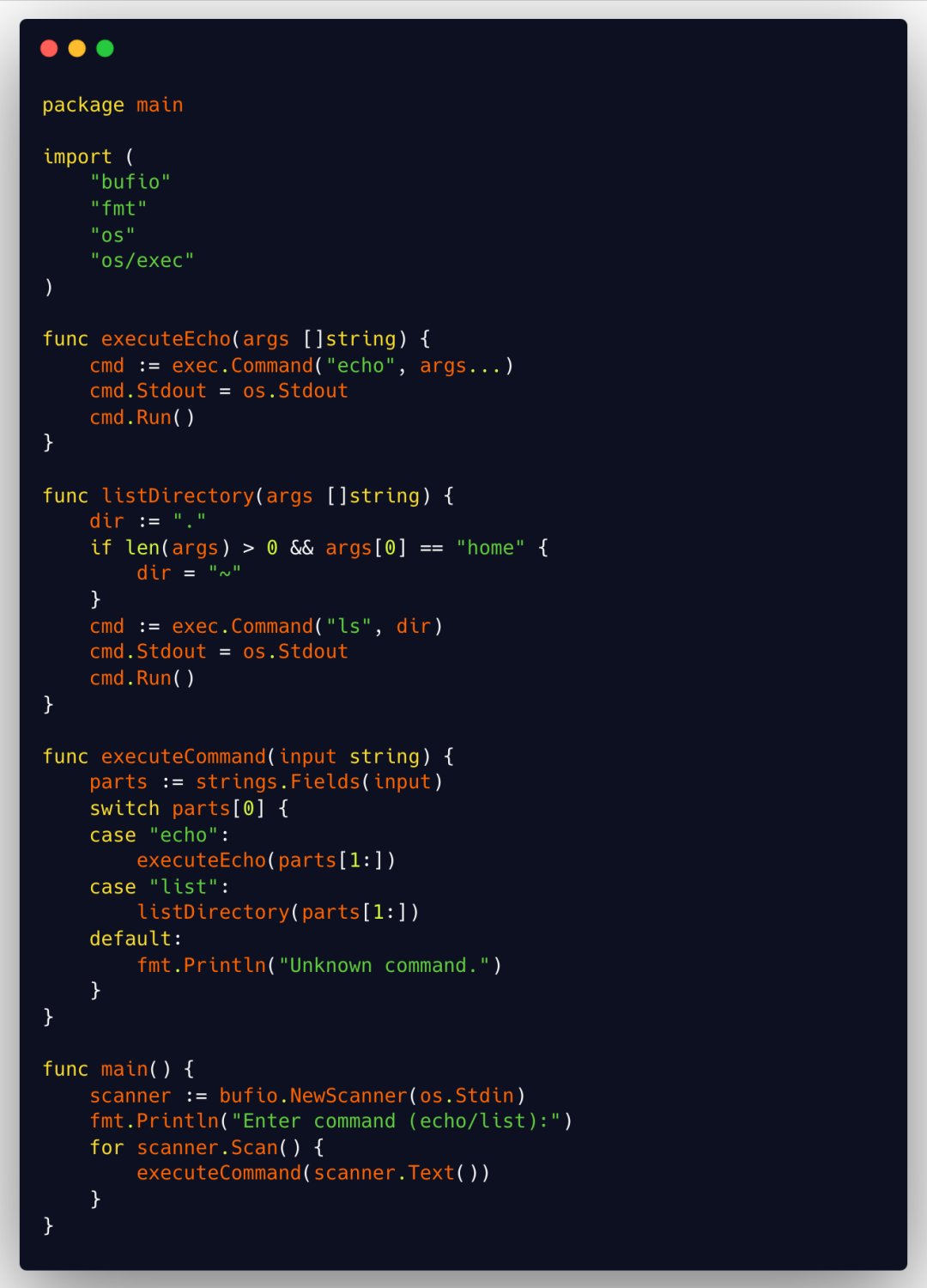
- The cyclomatic complexity is significantly reduced by breaking down the original executeCommand function into smaller functions (
executeEchoandlistDirectory). - Each function is responsible for a specific task, making the code more readable and easier to maintain.
- Although the use of
exec.Commandstill poses risks. Separating commands into dedicated functions allows for more controlled and secure user input handling.
Optimal Cyclomatic Complexity Values
The ideal values for cyclomatic complexity vary depending on the context and programming language. Generally, a cyclomatic complexity value of 10 or less is desirable for maintaining clear and easily understandable code.
From my experience, cyclomatic complexity values can be categorized in terms of safety as follows:
- 1-10: Regarded as an ideal range. Code within this range is typically easy to understand and maintain. Testing is more straightforward, and the likelihood of introducing security flaws is lower.
- 10-20: Indicates moderate complexity. While not ideal, it’s manageable. Rigorous testing and code reviews are important to ensure quality and security.
- 20-40: Considered a high level of complexity. Code in this range can be challenging to understand and test properly, increasing the risk of errors and vulnerabilities.
- > 40: Extremely complex and should be avoided. The code is difficult to understand and test, significantly increasing the risk of errors and security vulnerabilities.
These values should not be taken as strict rules but as general guidelines. Cyclomatic complexity should be assessed in the specific code and project context.
Mitigation and Best Practices
Cyclomatic complexity is often not considered a metric for secure software development. However, it is an important metric that can significantly impact software security. As demonstrated in the previous examples, high cyclomatic complexity can increase the likelihood of errors and security vulnerabilities.
Although it’s straightforward, the process for measuring cyclomatic complexity and its mitigation can vary depending on the programming language and available tools. Implementing it, however, can be more complex and, in some cases, require significant changes to the code.
Measuring Cyclomatic Complexity
Measuring cyclomatic complexity is the first step in addressing this issue. Some tools can help measure the cyclomatic complexity of code. Some of these tools include:
- Python: Radon is an excellent tool for Python. It analyzes source code to calculate cyclomatic complexity, among other metrics like maintainability index. Flake8 can also be used with options to measure cyclomatic complexity.
- Java: Use Checkstyle with its cyclomatic complexity module. This tool helps adhere to specific coding standards in Java and can calculate cyclomatic complexity for methods and classes.
- JavaScript: ESLint is a solid choice for JavaScript. Known more as a linter for finding and fixing code issues, it can also be configured to report on cyclomatic complexity.
- C++: Cppcheck is a static analysis tool that can be used to measure cyclomatic complexity and detect various types of code errors.
- C#: Visual Studio offers integrated capabilities to analyze cyclomatic complexity directly in the development environment for C#.
- PHP
- MD (PHP Mess Detector) helps find coding issues in PHP, including cyclomatic complexity.
- PHP - PhpMetrics provides a detailed analysis of PHP code quality, including cyclomatic complexity and other relevant metrics.
- Golang
- Gocyclo is specifically designed to calculate the cyclomatic complexity of functions in Go.
- Golang - Go Report Card, while broader in its functions, includes a review of cyclomatic complexity as part of its Go code analysis.
Mitigation Measures and Best Practices
To address cyclomatic complexity and its implications in cybersecurity, the following measures and best practices can be implemented:
- Code Refactoring: Regularly review and simplify code.
- Rigorous Testing: Implement automated and manual testing to identify and correct errors.
- Software Design Principles: Apply principles like SOLID to create more modular and maintainable code.
- Training: Many developers are unfamiliar with cyclomatic complexity and its impact on security. Training on this topic can help teams understand and address cyclomatic complexity.
- Code Review: Conduct regular code reviews to identify and correct complexity issues.
- Static Analysis Tools: Use static analysis tools to identify high-risk areas.
- Automated Security Testing: Implement automated security testing to detect vulnerabilities.
The priority order of these measures may vary depending on the context and specific needs of the project. However, if I had to choose one measure, it would be refactoring those parts of the code that are directly linked to user inputs, as this is where most vulnerabilities are found.
Conclusions
Cyclomatic complexity is a somewhat unknown metric in software development, but it’s an important one that can significantly impact software security.
This metric is often overlooked as a good practice in secure software development, but it’s an important one that can significantly impact software security.
Measuring cyclomatic complexity is straightforward, and some tools can help measure the cyclomatic complexity of code. However, its implementation can be more complex and, in some cases, require significant changes to the code. Even in the worst-case scenario, with measurement, we will know which parts of the code are more complex and, therefore, more prone to errors and potential vulnerabilities, allowing us to prioritize and focus our efforts on the most critical areas.


