DevSecOps series No. 1 — Breaking the CI/CD by using evil Git repositories
This is the first post of a serie about DevSecOps. We’ll discuss about (in)security in DevSecOps process.
Today we’ll check security in building process when you need external GIT.
GIT in the CI process
Cloning GIT repositories is an usual task for a CI pipeline when you’re building artefacts. Some programming languages do more use of GIT for the building process. For examples, in GoLang you can set dependencies as Github URL:
package main
import (
"github.com/spf13/cobra"
"github.com/pkg/errors"
)
func main() {
...
}
This is a very common task in a CI process. Nothing strange there.
Evil GIT repositories
Software bombs are a very old concept in computer security. As you can imagine, Git bomb idea is also exist.
From 2017 there’s available a PoC for Git Bomb. You can get more info in the author web site: https://kate.io/blog/git-bomb/
Basically, Git Bomb is a special Git repository that was made to break down the Git Cloning process and never ending.
Testing Git Bomb attack
If some of each repository of your building process depends was compromised (or if the author is a “funny guy”) when you try to clone your CI machine will be break down.
In the best case (if your C.I. machine was hardened) the process will end when timeout will be reached.
Here you can see an example when we try to clone a Git Bomb PoC repository:
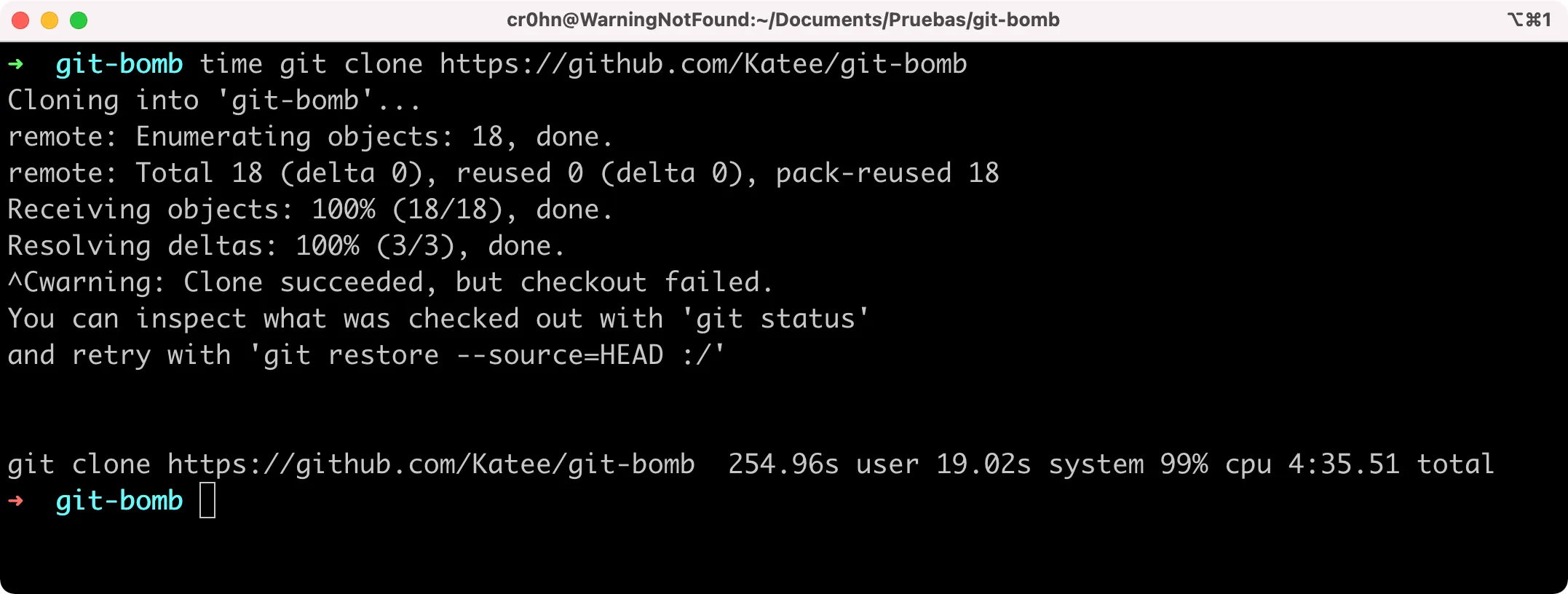
Process was cancelled after it took 4 minutes.
Also you can check that the CPU consumption was very high (near 100%):
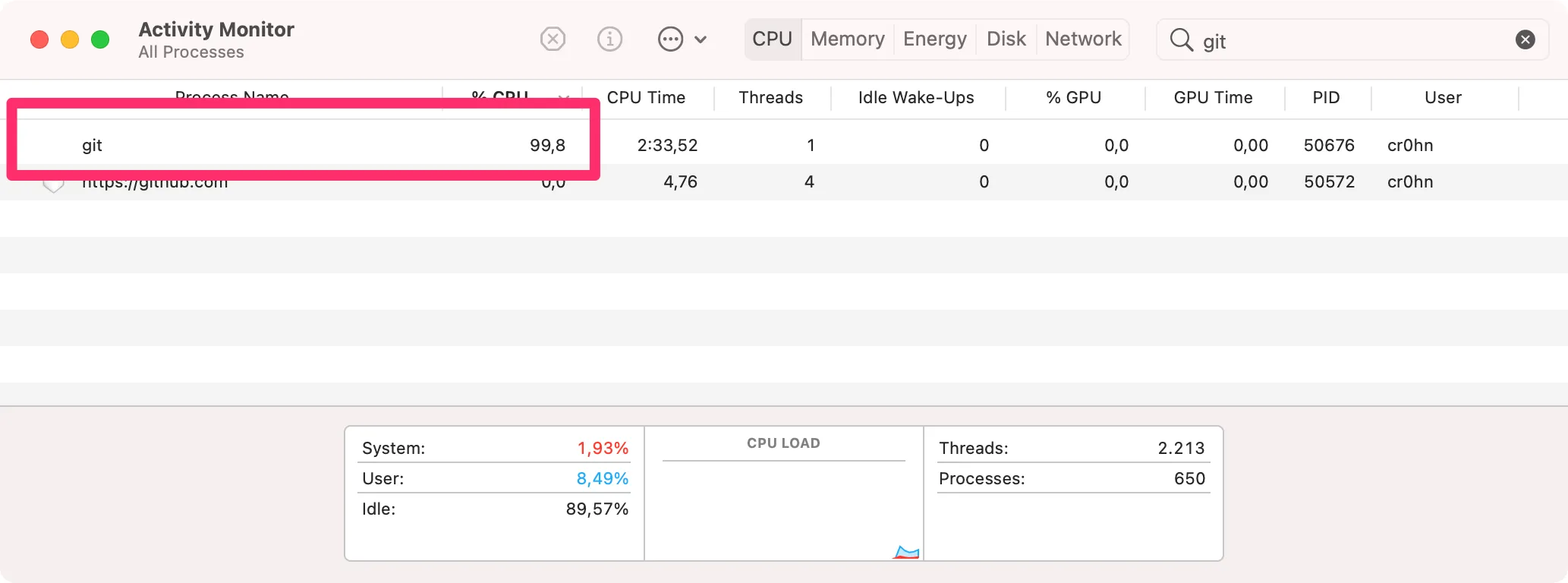
Don’t be evil and don’t do this at home 😜